Not all malicious activity is detectable by reviewing the headers as often hackers hide their attack in the attachments of an email.
ATTACHMENT TIPS
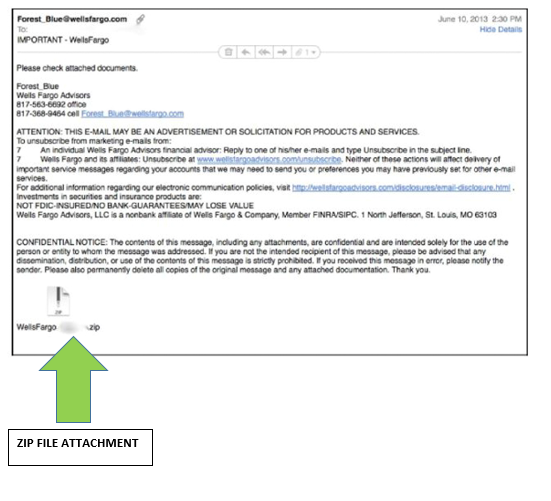
First, if you receive a compressed file, such as a file that ends in .zip, you should be very careful. Because of the way compression works, the file content may be very malicious indeed but not be detectable by automated means. For example, the following email has an attachment that is zipped.
Without executing the Unzip process, it is difficult to know what is in the attachment. This problem is true of all file types, particularly since some file types can be cleverly disguised as other file types. What you think might be a DOC file might actually be an EXE file. So, the rule of thumb with all attachments is to be extremely cautious.
In this case, your best bet is to follow these steps:
• First, examine the headers. Is this message from someone you know, really? Even if the answer is yes, do not open the attachment yet! If the answer is no, delete the email.
• Second, examine the source of the message: does it appear to be legitimate once you look at the internals? Even if the answer is yes, do not open the attachment yet! If the answer is no, delete the email.
• Finally, if the email appears to be legitimate and you are really tempted to open the attachment, do not do that until you have contacted the sender and verified that he or she actually sent you that zipped file. However, it is best to check via the phone or SMS since it is possible that the correspondent’s account has been hacked.
Once you have decided that it is probably okay to open an attachment, there are safer ways to open an attachment than simply double-clicking and launching the attachment. It is best to save the file to disk and then open it from a limited functionality application, such as a basic text editor.
There are legitimate and important reasons to send attachments, but attachments can also be dangerous. Zipped files can hide attacks, but so can any number of other file types. Within the last several years, researchers discovered that it was possible to hide attacks within PDF files, which had been considered to be fairly safe.
EMAIL ENCRYPTION
The CYBONET Email Encryption allows users to send password protected PDFS with a clientless encryption solution that is policy based and automated. Passwords are shared either by SMS, email or manually meaning attachments can be sent and opened safely.
For more information on Email Encryption and/or CYBONET please visit our website www.cybonet.com or contact This email address is being protected from spambots. You need JavaScript enabled to view it.